Privacy-preserving Data Analytics for Environmental Public Health
- Research Overview
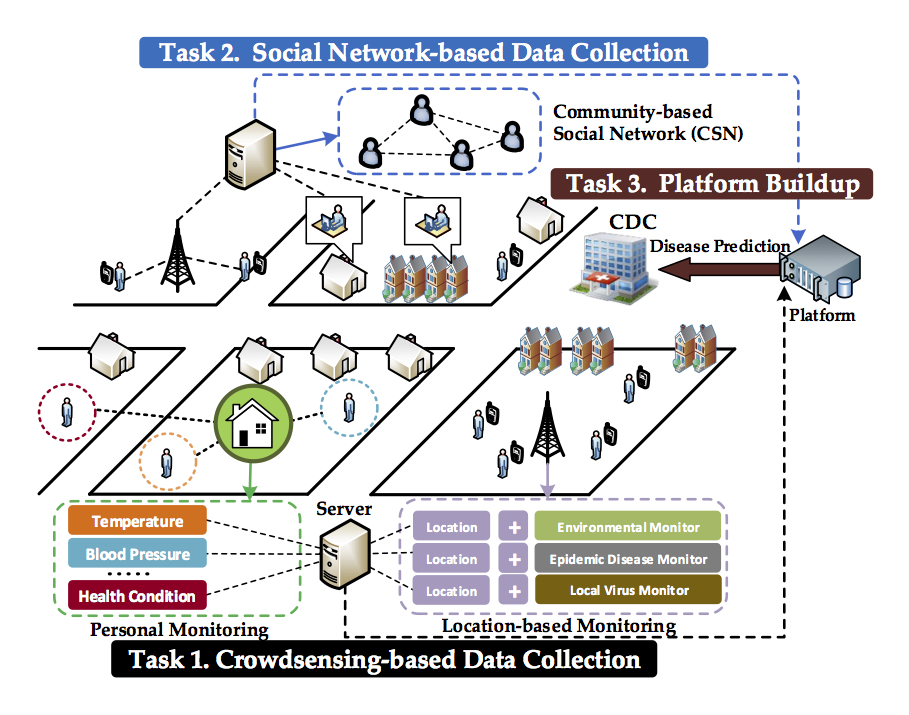 Healthcare systems have been revolutionized in recent years, which enable smart medical care to help improve public health for millions of people in the United States. Although current healthcare systems actively collect patients' medical data, numerous personal subjective data is commonly neglected in the analysis of environmental public health. This is, to a large extent, due to high-sensitivity of health-related data, and people, especially patients, are reluctant to report their health conditions for public health. As a result, there is a lack of real-time monitoring data, such as symptom reports from high-risk groups and severe environmental pollution in local communities, that causes notoriously long latency for effective prevention of the spread of epidemic diseases. This project is to address the fundamental challenges on collecting and analyzing multi-scale data from multi-sources for environmental public health in a privacy-preserving manner.
Healthcare systems have been revolutionized in recent years, which enable smart medical care to help improve public health for millions of people in the United States. Although current healthcare systems actively collect patients' medical data, numerous personal subjective data is commonly neglected in the analysis of environmental public health. This is, to a large extent, due to high-sensitivity of health-related data, and people, especially patients, are reluctant to report their health conditions for public health. As a result, there is a lack of real-time monitoring data, such as symptom reports from high-risk groups and severe environmental pollution in local communities, that causes notoriously long latency for effective prevention of the spread of epidemic diseases. This project is to address the fundamental challenges on collecting and analyzing multi-scale data from multi-sources for environmental public health in a privacy-preserving manner. - Research Objective
This multidisciplinary research advances the state-of-the-art public health by combining multi-scale data collection and analysis. Specifically, the project redesigns current healthcare monitoring systems for both severe infectious diseases (e.g., SARS, H1N1, Ebola, etc.) and long-term environment-related diseases and their exacerbation (e.g., air pollutant-induced pulmonary diseases, such as chronic obstructive pulmonary disease (COPD) and lung cancer). This project addresses the privacy preservation in two-fold: 1) completely redesign efficient collaborative classification schemes by applying novel metrics without leaking individual's privacy; 2) introduce new architectures to perform crowdsourcing data analysis by using light-weighted and verifiable encryption schemes. A new methodology on public health prediction model will be developed with practical systematic implementation in healthcare systems.
- Research Team
- Faculty, Dr. Linke Guo@Binghamton University; Collaborator, Dr. Yuguang Fang@University of Florida and Dr. Guirong Wang@Upstate Medical University, SUNY
- Student, Qi Jia@Binghamton University
- Acknowledgement
This project is supported in part by the U.S. National Science Foundation (NSF) under the grant IIS-1722731 ($307,999, 9/1/2017-8/31/2021). Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the NSF.
Malicious Behavior Detection in Hybrid Dynamic Spectrum Access
- Research Overview
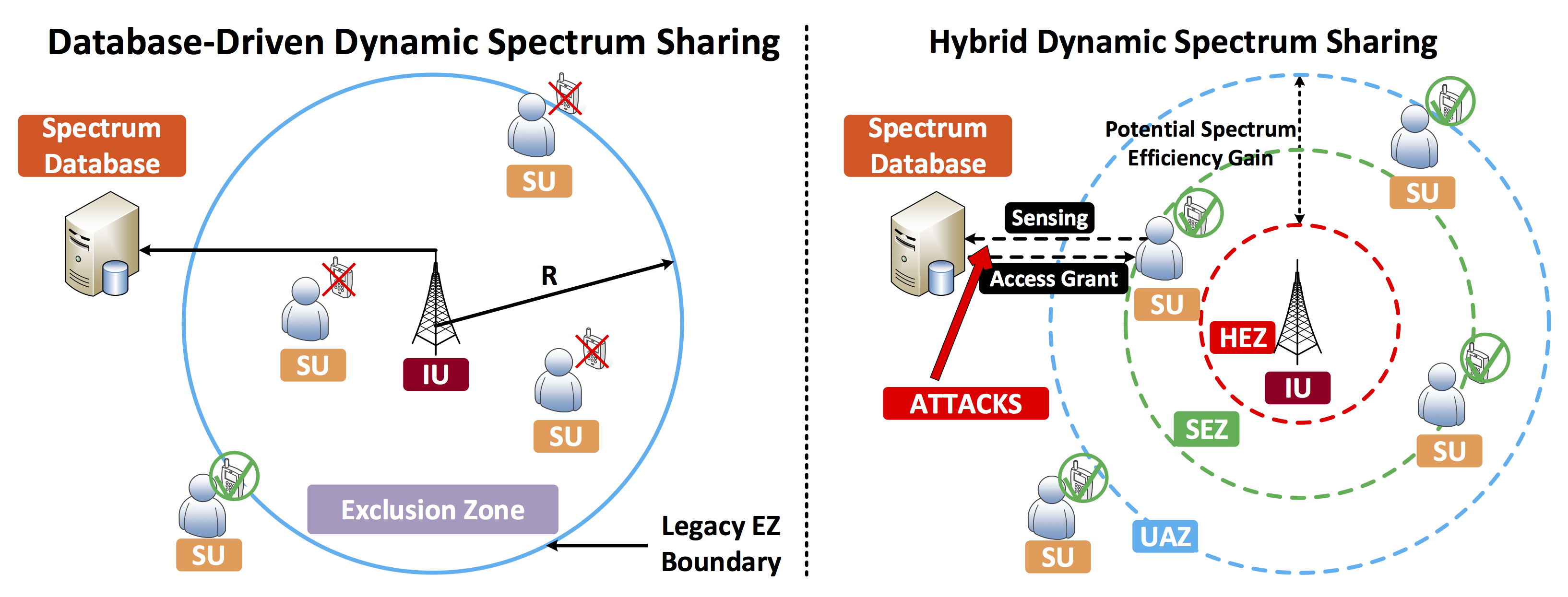 To tackle the ever-increasing spectrum scarcity issue, dynamic spectrum access is envisioned as a set of promising new spectrum management paradigms. Although it has enabled the opportunistic access of underutilized licensed bands, various practical factors hinder it from wide deployment. The recently released FCC rules suggest participatory real-time spectrum sensing can greatly improve the spectrum utilization efficiency for database-driven spectrum sharing, which forms a new paradigm, hybrid dynamic spectrum sharing. However, the frequent information exchanged between secondary users and spectrum database can be easily intercepted and manipulated by malicious users. This project will explore new paradigms of safeguarding the future cognitive radio system with focus on non-compliance behavior detection.
To tackle the ever-increasing spectrum scarcity issue, dynamic spectrum access is envisioned as a set of promising new spectrum management paradigms. Although it has enabled the opportunistic access of underutilized licensed bands, various practical factors hinder it from wide deployment. The recently released FCC rules suggest participatory real-time spectrum sensing can greatly improve the spectrum utilization efficiency for database-driven spectrum sharing, which forms a new paradigm, hybrid dynamic spectrum sharing. However, the frequent information exchanged between secondary users and spectrum database can be easily intercepted and manipulated by malicious users. This project will explore new paradigms of safeguarding the future cognitive radio system with focus on non-compliance behavior detection. - Research Objective
This first research task will identify new attack models that compromise the spectrum efficiency and then provide countermeasures adapted to future wireless systems. Due to the inherent nature of database-driven spectrum access, primary user emulation (PUE) attackers can retrieve the spectrum availability information to either perform as the incumbent user (IU) when it is not present, or try to increase secondary users' transmission power to interfere with present IUs. Featuring the sensing results stored in the database, novel detection schemes will be designed to mitigate the influence brought by the attack.
The second research task leverages physical-layer approaches to detect unauthorized access under different channel models. To address this issue, channel availability information will be used to detect malicious secondary users. Meanwhile, the detection mechanisms will be developed with joint consideration on practicality and efficiency. Additionally, the project includes strong validation component that combines simulation study, prototyping, and experimentation.
- Research Team
- Faculty, Dr. Linke Guo@Binghamton University
- Student, Xiaonan Zhang@Binghamton University
- Selected Publication
- Xiaonan Zhang, Qi Jia, and Linke Guo, ``Secure and Optimized Unauthorized Secondary User Detection in Dynamic Spectrum Access''. IEEE Conference on Communications and Network Security (CNS 2017), Las Vegas, NV, Oct. 9-11, 2017. (Accept Ratio: 29.9%).
- Jiajun Xin, Ming Li, Linke Guo, and Pan Li, ``Practical Privacy-Preserving Spectrum Query Schemes for Database-Driven CRNs with Multiple Service Providers''. IEEE Conference on Communications and Network Security (CNS 2017), Las Vegas, NV, Oct. 9-11, 2017. (Accept Ratio: 29.9%).
- Acknowledgement
This project is supported in part by the U.S. National Science Foundation (NSF) under the grant CNS-1744261 ($150,000, 9/1/2017-8/31/2019). Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the NSF.
Privacy-preserving Mobile Crowdsensing
- Research Overview
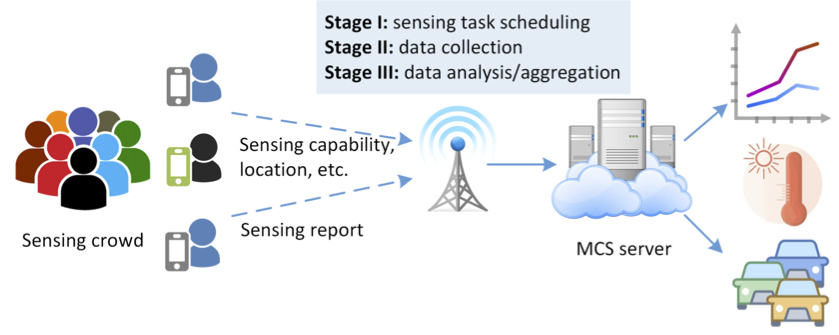 Mobile devices, including smartphones and tablets, are becoming extremely prevalent nowadays. Equipped with diverse sensors, from GPS to camera, and paired with the inherent mobility of their owners, mobile devices are capable of acquiring rich information of surrounding environment. However, the wide adoption of mobile crowd sensing is largely hindered by its privacy concerns. The overall goal of this project is to address privacy leakage issues from different stages of mobile crowd sensing. Privacy-enhanced mobile crowd sensing will attract more participants and thus accelerate the maturity of smart health care, environment monitoring, traffic surveillance, social event observation, etc.
Mobile devices, including smartphones and tablets, are becoming extremely prevalent nowadays. Equipped with diverse sensors, from GPS to camera, and paired with the inherent mobility of their owners, mobile devices are capable of acquiring rich information of surrounding environment. However, the wide adoption of mobile crowd sensing is largely hindered by its privacy concerns. The overall goal of this project is to address privacy leakage issues from different stages of mobile crowd sensing. Privacy-enhanced mobile crowd sensing will attract more participants and thus accelerate the maturity of smart health care, environment monitoring, traffic surveillance, social event observation, etc. - Research Objective
Thrust I explores protecting user's sensitive information, such as locations, sensing capabilities and task preferences, from the server, while still allowing it to optimally or approximately solve task allocation problems. Rather than highly computationally-intensive crypto-based techniques, privacy preservation schemes will be designed based on decomposition methods and distributed computing algorithms.
Thrust II aims to provide user's location privacy in the stage of data collection. Since locations of users, who perform sensing over the same event within a certain geographic area, are highly correlated, it deteriorates user's privacy achieved individually. To address this issue, privacy preservation schemes will be developed by exploring collaborations among users. Game theories will be adopted to further analyze users' strategies and interactions.
The objective of Thrust III is to protect users' sensing data privacy during the stage of data analysis. The research is featured by jointly considering the data imperfection that is caused by the limited sensing capabilities at mobile devices and even the misbehavior of lazy/malicious users. To achieve data privacy and service accuracy simultaneously, novel schemes will be developed combining efficient matrix completion methods and advanced crypto techniques.
- Research Team
- Faculty, Dr. Linke Guo@Binghamton University; Collaborator, Dr. Ming Li@University of Nevada Reno
- Student, Pei Huang@Binghamton University
- Selected Publication
- Xiaonan Zhang, Qi Jia, and Linke Guo, ``Secure and Optimized Unauthorized Secondary User Detection in Dynamic Spectrum Access''. IEEE Conference on Communications and Network Security (CNS 2017), Las Vegas, NV, Oct. 9-11, 2017. (Accept Ratio: 29.9%).
- Jiajun Xin, Ming Li, Linke Guo, and Pan Li, ``Practical Privacy-Preserving Spectrum Query Schemes for Database-Driven CRNs with Multiple Service Providers''. IEEE Conference on Communications and Network Security (CNS 2017), Las Vegas, NV, Oct. 9-11, 2017. (Accept Ratio: 29.9%).
- Acknowledgement
This project is supported in part by the U.S. National Science Foundation (NSF) under the grant ECCS-1710996 ($150,000, 9/1/2017-8/31/2020). Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the NSF.
